Why this question matters (and why lawyers and engineers answer it differently)
At first glance, the question sounds trivial: “If faces are blurred, the video is anonymized, right?”
In practice, this assumption is responsible for a huge amount of legal risk, broken systems, and false confidence in video-based products.
The core problem is simple: lawyers think in definitions, engineers think in transformations – and blurred video sits exactly at the intersection where these two worldviews clash.
The engineering reality: identity is more than a face
From a technical perspective, a human identity in video is distributed across multiple signals, not just facial features.
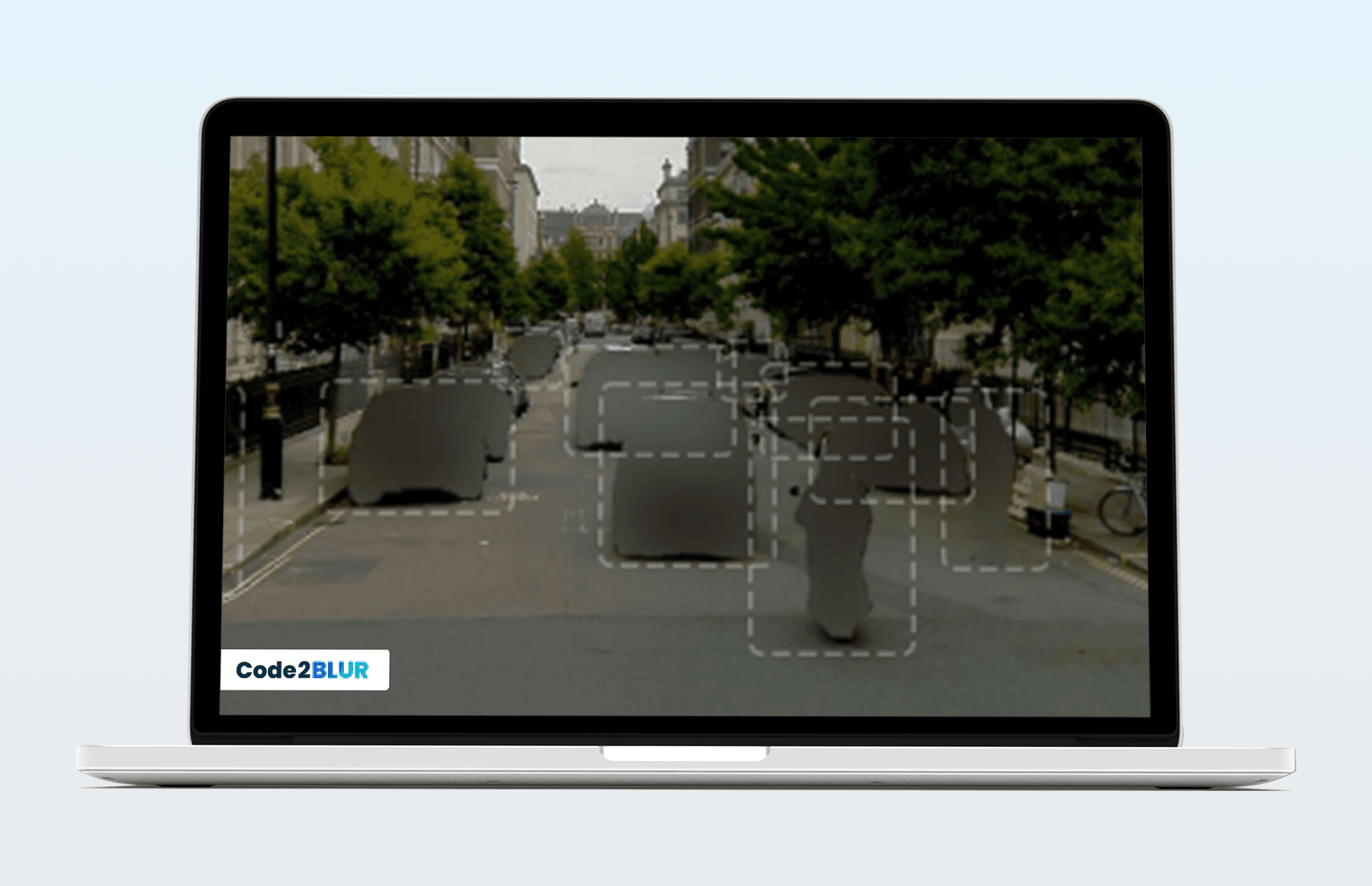
Even after blurring faces, video can still contain:
- body shape and proportions
- gait and movement patterns
- clothing, uniforms, accessories
- tattoos, scars, posture
- spatial and temporal context (where and when)
- correlations across frames and cameras
Blurring removes one class of features, but leaves many others untouched.
For engineers working with computer vision, this creates an uncomfortable truth: A blurred video can still uniquely describe a person.
And uniqueness is often enough for identification – especially in constrained environments.
Why this matters in real systems
In CCTV systems and smart city analytics platforms, blurring is often treated as a clear boundary between personal and anonymous data. Once applied, the footage is commonly assumed to be safe for broader use, even though this assumption is rarely validated from a technical perspective. As a result, blurred video starts circulating within the organization as “low-risk” data, despite the fact that it may still allow individuals to be identified under certain conditions.
In practice, this typically leads to:
- sharing video footage with a wider range of internal teams and external partners,
- using blurred video for analytics and machine learning training without additional safeguards,
- applying longer data retention periods because the data is considered non-sensitive,
- weaker access control, monitoring, and audit practices around video usage.
The core question this article answers
So the real question is not: “Is blurred video anonymous?” The real question is: “After blurring, can a person still be identified – directly or indirectly – using the remaining signals and realistic attack models?”
This article answers that question from a technical perspective, by:
- breaking down what blur actually removes (and what it doesn’t),
- showing realistic re-identification paths,
- and providing engineering criteria instead of vague assurances.
Key definitions engineers should care about
Before assessing whether blurred video is still personal data, it is necessary to align on terminology. Not because definitions are an academic exercise, but because system design decisions often hinge on how these terms are interpreted. In video-based systems, misunderstandings around concepts such as personal data, anonymization, or identifiability routinely lead to architectural shortcuts that later become compliance, security, or scalability problems.
For engineers, the goal is not to memorize legal language, but to understand how these definitions translate into system behavior, threat models, and data flows.
Personal data vs anonymous data (practical interpretation)
From a practical standpoint, personal data is any information that allows a natural person to be identified, either directly or indirectly. In video systems, indirect identification is far more common than direct identification. A single frame may not reveal a name or a face, but video rarely exists in isolation. It is recorded at a specific place, at a specific time, often repeatedly, and usually in an environment with a limited number of possible individuals.
Anonymous data, on the other hand, is not simply data without obvious identifiers. It is data where identification is no longer realistically possible using reasonable means. This distinction is critical. Absolute impossibility is not required; what matters is whether identification can still occur in practice, given typical access, tools, and contextual knowledge.
In video systems, identifiability often emerges from a combination of signals rather than a single feature. These signals may include:
- spatial and temporal context (where and when the recording was made),
- recurring patterns across frames or multiple recordings,
- physical characteristics such as body shape, posture, or movement,
- environmental cues such as uniforms, vehicles, or restricted locations,
- correlations with other datasets available to the organization.
When such signals remain intact, the video output should still be treated as personal data, regardless of whether faces or license plates have been blurred.
If a person can still be singled out, linked across time, or distinguished within a limited group, the data is unlikely to be truly anonymous in practice.
Pseudonymization vs anonymization vs masking
In technical discussions, these three terms are often used interchangeably, which is a major source of confusion. From a systems perspective, they describe fundamentally different outcomes.
Pseudonymization replaces direct identifiers with alternative values while preserving the ability to link data back to the same individual. In video analytics, this often appears as persistent tracking IDs assigned to people across frames or sessions. While faces may be blurred, the system still “knows” that the same person appears repeatedly. This approach improves privacy but does not remove the data from the scope of personal data.
Anonymization aims to eliminate the possibility of identifying an individual altogether, including indirect identification. This requires more than hiding visible features. It demands that the system output no longer supports re-identification through context, correlation, or auxiliary data. In video pipelines, achieving this reliably is difficult and usually requires deliberate architectural choices rather than a single post-processing step.
Masking, including traditional blurring, is a visual obfuscation technique. It reduces the visibility of certain attributes to human viewers but does not guarantee that the underlying information content is sufficiently degraded. In many cases, masking affects only one class of identifiers while leaving others untouched.
From an engineering point of view, the distinction can be summarized as follows:
- pseudonymization reduces exposure but preserves linkage,
- anonymization removes identifiability entirely,
- masking modifies appearance without guaranteeing either outcome.
Masking is a technique. Anonymization is a property. Confusing the two leads to false assumptions about risk.
“Reasonably likely to identify” – what it means in systems terms
One of the most misunderstood concepts in data protection is the idea of identification being “reasonably likely.” Engineers sometimes interpret this as protection against only the most basic or unsophisticated attacks. Others assume it refers to adversaries with unlimited resources. In reality, it sits somewhere in between and must be evaluated in the context of the system being built.
From a systems perspective, “reasonably likely” depends on who has access to the data, what contextual knowledge they possess, and how easily the data can be combined with other sources. An internal analyst with access to location metadata, historical footage, or operational schedules may be far more capable of identifying individuals than an external attacker with only a single video clip.
Key questions engineers should ask include:
- Who can access the processed video outputs?
- What contextual information do they already have?
- Can the same individual be tracked across time or cameras?
- Are there auxiliary datasets that can be correlated with the video?
- How much effort is required to perform such correlation in practice?
If identification does not require extraordinary effort, specialized equipment, or implausible assumptions, it should be considered reasonably likely.
If identification is feasible for someone who realistically interacts with the system, the data should be treated as personal — even if it looks anonymized at first glance.
What “blur” actually does to information
Blurring is often described as “removing information” from video. In reality, blur is a selective degradation of certain visual features, not a neutral erasure of identity. To understand why blurred video can still be personal data, it is essential to look at what blur changes, what it leaves untouched, and how those remnants can still be exploited.
Common blur types: Gaussian, mosaic, box blur
Different blur techniques are frequently treated as interchangeable, but they affect information in different ways. All of them reduce high-frequency detail, yet none of them fully eliminate structural or contextual signals.
Gaussian blur smooths pixel values using a weighted average, producing soft transitions and visually pleasing results. It hides fine details such as facial features, but preserves overall shapes, edges, and motion patterns. Because it is continuous, it often leaves enough signal for tracking and re-identification across frames.
Mosaic or pixelation works by grouping pixels into larger blocks and replacing them with a single color or average value. While this makes individual features harder to see, it preserves coarse structure and relative proportions. With weak pixelation, modern models can still infer shape and movement; with strong pixelation, the video may become unusable for its original purpose.
Box blur applies a uniform average across a fixed window. It is computationally cheap and commonly used in real-time systems, but from an information perspective it behaves similarly to Gaussian blur, only with harsher edges. Like other blur types, it suppresses detail without addressing higher-level identity cues.
Key takeaway: Different blur methods change how information is degraded, but none of them guarantee loss of identifiability on their own.
What information survives blurring (and why it’s important)
Even after aggressive blurring, video retains a surprising amount of usable information. This is because identity in video is not encoded solely in fine-grained detail. Instead, it is spread across multiple layers of signal that blur does not target.
Common examples of information that typically survives blurring include:
- body shape, proportions, and relative size,
- gait, posture, and movement dynamics,
- clothing, uniforms, and carried objects,
- spatial position within a scene,
- temporal patterns such as arrival times or repeated behavior.
These features are particularly powerful when combined across frames. A blurred face in a single image may reveal little, but a blurred person moving through a scene over time can still be uniquely described and tracked.
Key takeaway: Blur hides detail, but it rarely removes the structure needed for indirect identification.
Blur vs resolution vs bitrate: hidden side channels
Blur is often applied without considering other parameters that influence information leakage. Resolution, compression, and bitrate can all act as side channels that undermine the intended effect of blurring.
High-resolution video that is lightly blurred may still contain recoverable structure, especially when viewed frame by frame or processed by models trained on degraded inputs. Similarly, compression artifacts can preserve motion vectors or block patterns that aid tracking. Even when visual clarity is reduced, temporal consistency across frames can remain intact.
In practice, this means that blur cannot be evaluated in isolation. A heavily blurred, low-resolution, aggressively compressed stream may behave very differently from a lightly blurred, high-bitrate feed — even if both appear “blurred” to the human eye.
Key takeaway: Anonymization is a property of the entire video pipeline, not just a single visual filter.
When blurred video is still personal data (common engineering patterns)
Blurring is often applied correctly at a visual level, yet the resulting footage still qualifies as personal data. The reason is usually not a faulty implementation, but an overly narrow understanding of where identity actually resides in video. In practice, identity signals frequently survive even when faces are no longer visible.
Faces blurred, but unique body features remain
Face-only blurring removes the most obvious identifier, but leaves many others intact. Body shape, proportions, posture, gait, and clothing often remain stable enough to distinguish individuals – especially in environments with a limited number of people.
This effect is amplified over time. Even without faces, tracking across frames or cameras allows systems to build persistent identities based on movement and behavior patterns.
Partial masking: face only vs full-body anonymization
Partial masking assumes that identity is localized to specific regions, typically the face. In reality, identity in video is distributed across the entire person and their interaction with the scene.
Full-body anonymization aims to reduce this residual signal by modifying or replacing the entire person representation. While more complex, it significantly lowers the risk of indirect identification and cross-frame linkage.
Face-only blur vs full-body anonymization
| Aspect | Face-only blurring | Full-body anonymization |
|---|---|---|
| Visible identity cues | Body shape, gait, clothing remain | Most physical cues suppressed |
| Cross-frame tracking | Typically possible | Significantly harder |
| Contextual identification | High | Reduced |
| Analytical usefulness | High | Medium to task-specific |
| Re-identification risk | High in constrained settings | Much lower |
| Typical use | Compliance-driven masking | Privacy-by-design systems |
When blurred video might qualify as anonymous (and what must be true)
Blur alone rarely makes video anonymous. That said, there are situations where blurred or otherwise transformed video may reasonably be treated as anonymous data — but only if several technical conditions are met simultaneously. Anonymity is not achieved by a single operation; it is an emergent property of the entire pipeline.
The key question is not “Did we blur enough?”, but rather: “What identification paths still exist after all transformations and controls are applied?”
Irreversibility and robust de-identification across frames
The first condition is irreversibility — not just visually, but operationally. It must be infeasible to reconstruct identifying features from the output, even when considering modern reconstruction and enhancement techniques.
Just as important is de-identification across time. A single anonymized frame is rarely the problem. Persistent identity usually emerges when the same individual can be linked across multiple frames or cameras. If tracking, linkage, or stable identifiers survive the transformation, the data is unlikely to be anonymous.
In practice, this means:
- no stable person IDs across frames,
- no consistent silhouettes or motion signatures that enable tracking,
- no ability to correlate appearances over time.
If the system can still “recognize” the same person twice, anonymity is probably not achieved.
Removing or neutralizing context and metadata
Even when visual cues are heavily degraded, context can reintroduce identifiability. Location, time, camera placement, and operational metadata often narrow the set of possible individuals dramatically.
To meaningfully reduce risk, contextual signals must be neutralized or abstracted. This may involve removing precise timestamps, generalizing locations, stripping camera identifiers, or avoiding release of raw scene context altogether.
Common contextual leakage sources include:
- exact timestamps and event logs,
- fixed camera locations tied to known spaces,
- metadata embedded in video containers,
- predictable recording schedules.
If someone can identify where and when the video was recorded, identifiability may still exist — even without visual detail.
Threat model aligned with real adversaries (internal and external)
Anonymity cannot be assessed in a vacuum. It must be evaluated against a realistic threat model that reflects who can access the data and what they already know.
Internal users often pose a higher re-identification risk than external attackers. They may have access to building layouts, staff schedules, historical footage, or operational knowledge that makes indirect identification trivial.
A useful engineering exercise is to ask:
- Who can realistically access the processed video?
- What auxiliary knowledge do they already possess?
- How much effort would re-identification require in practice?
If identification is easy for any realistic actor interacting with the system, the data should not be treated as anonymous.
Rule of thumb: Design for the strongest realistic adversary, not the weakest theoretical one.
Residual risk and acceptable thresholds (engineering approach)
No anonymization process reduces risk to zero. The goal is to reduce identifiability below a threshold that is considered acceptable given the use case, scale, and impact.
From an engineering perspective, this means treating anonymity as a risk management problem, not a binary state. Teams should be explicit about what residual risk remains and why it is acceptable.
This typically involves:
- defining acceptable re-identification scenarios,
- documenting assumptions and threat models,
- validating transformations with practical tests,
- revisiting decisions as models and tools evolve.
If residual risk cannot be clearly articulated and defended, the data should still be treated as personal.